Gig Performer has OSC support and that’s very nice!
Starting to work with OSC often necessitates to monitor OSC messages like Gig Performer can do it for MIDI messages using its builtin MIDI monitor. Reading the GP forum, different software for OSC monitoring can be identified, among them:
- Protokol (for Windows, Mac, Linux, iOS & Android): Protokol | hexler.net (by the TouchOSC team)
- OSC Data Monitor (for Windows & Mac): https://www.kasperkamperman.com/blog/processing-code/osc-datamonitor/ (see also the nice OSC video introduction: https://youtu.be/0uOR2idKvrM)
- OSC Shark (cross platform source code of a QT-based clone of OSC Data Monitor): Oscshark
- OSC Monitor (for Windows): EyeCon - Video Motion Sensing
- OSCulator (for Mac but maintenance stopped in 2024): https://osculator.net/ => this one does much more than only OSC monitoring, see here OSCulator - convert any input to any output - Gig Performer®
The above list is a summary from GP forum posts from @pianopaul, @simon & @dhj.
Regarding OSC monitoring, I also wanted to share my experience of using a cross platform network packet analyzer for this purpose, namely Wireshark: https://www.wireshark.org/
I already knew Wireshark, but I didn’t immediatly came to the idea that Wireshark could “know” about the OSC protocol, and good news, it does ![]()
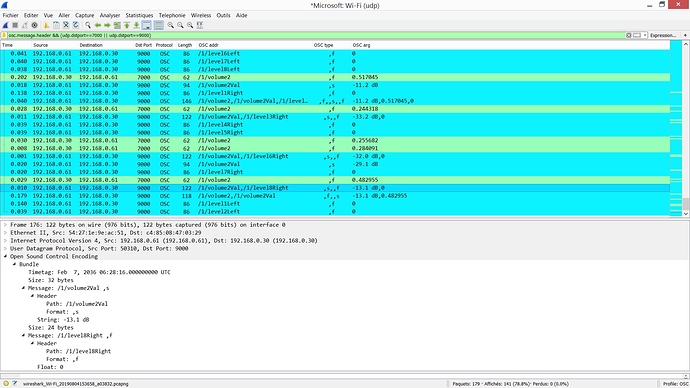
The advantage of using Wireshark for OSC monitoring is that it can monitor all the OSC devices at the same time without having to change anything to the IP adressing of your network. Here is an exemple of the Wireshark main window when monitoring an OSC communication between an RME audio interface and GP:
Wireshark offers many option to filter the display. Here I simply had:
osc.message.header && (udp.dstport==7000 || udp.dstport==9000)but I guess you imagine that it is quite simple to do much more.
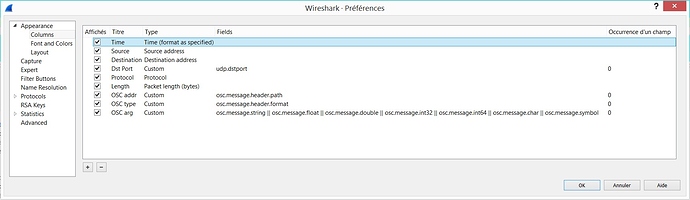
The column titles speak from themselves and you can even determine if the OSC messages are packed in an OSC bundle or not. Here are the corresponding columns settings:
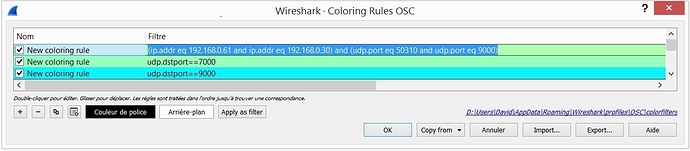
To make the OSC messages list even more readable you can customized the displayed colors. Here I changed the colors according to the UDP destination port :
So, also think of testing Wireshark for OSC monitoring, especially if you work with Windows and therefore cannot use OSCulator.